Wednesday, December 17, 2014
Wednesday, November 5, 2014
Tuesday, October 7, 2014
SOLUTION How to remove iStartSurf.com virus (Removal Guide)
iStartSurf is a browser hijacker, which is promoted via other free downloads, and once installed it will change your browser homepage to iStartSurf.com and default search engine tosearch.yahoo.com.
This in itself is not considered malicious as there are many legitimate programs that change these settings as well. What is considered malicious, though, is that it will also append the argument http://iStartSurf.com to random Windows shortcuts on your desktop and your Windows Start Menu.
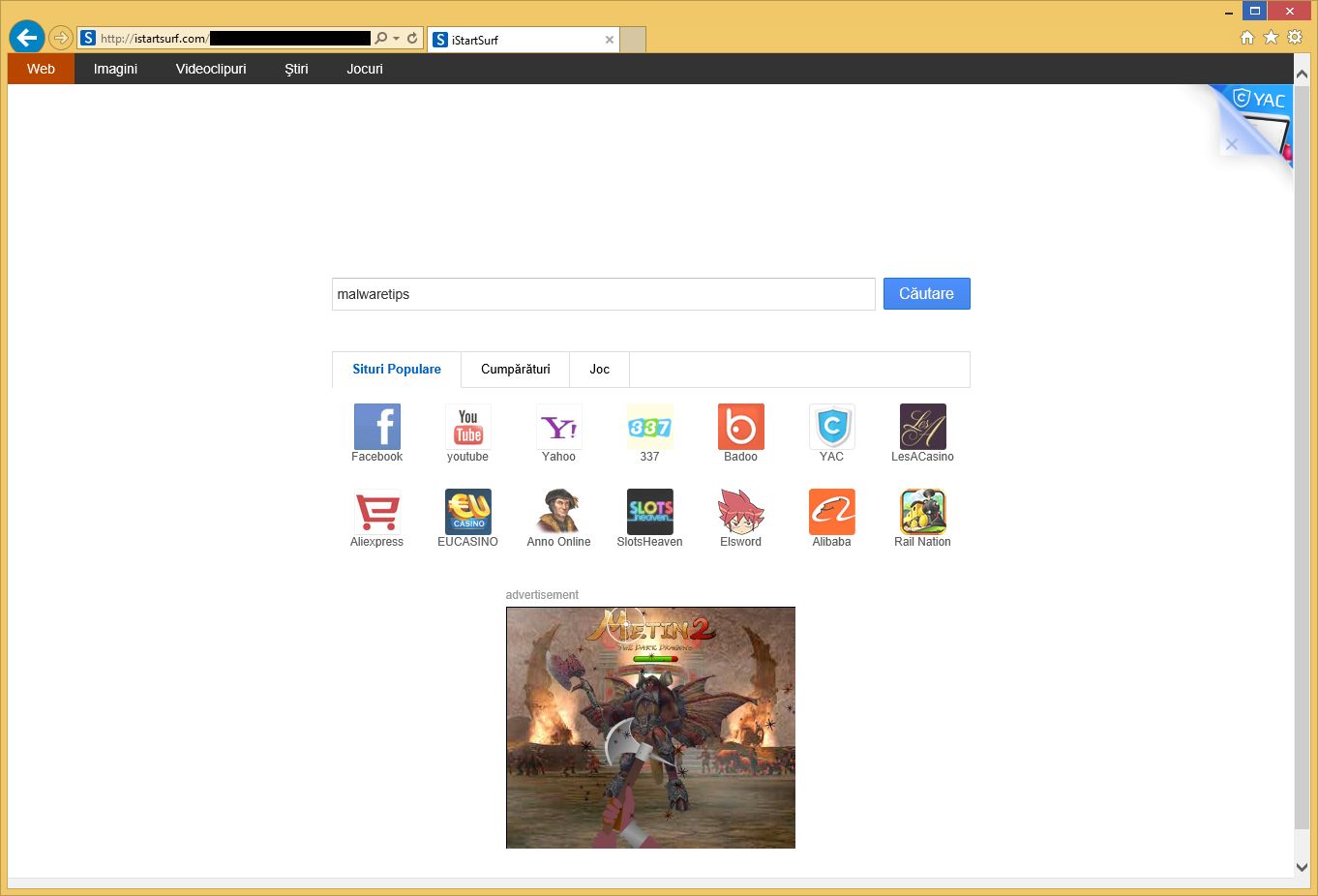
The iStartSurf.com homepage will display advertisements and sponsored links in your search results, and may collect search terms from your search queries. The iStartSurf.com hijack is used to boost advertising revenue, as in the use of blackhat SEO, to inflate a site’s page ranking in search results.
This in itself is not considered malicious as there are many legitimate programs that change these settings as well. What is considered malicious, though, is that it will also append the argument http://iStartSurf.com to random Windows shortcuts on your desktop and your Windows Start Menu.

The iStartSurf.com homepage will display advertisements and sponsored links in your search results, and may collect search terms from your search queries. The iStartSurf.com hijack is used to boost advertising revenue, as in the use of blackhat SEO, to inflate a site’s page ranking in search results.
iStartSurf it’s technically not a virus, but it does exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program.
iStartSurf is an ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer (BHO) and Firefox/Chrome (plugin) and distributed through various monetization platforms during installation. The browser extension includes various features that will modify the default or custom settings of the browser including the home page, search settings and in some cases will modify Internet Explorer’s load time threshold, place a lock file within Firefox to prevent competing software from changing its settings as well as disable the browser’s Content Security Policy in order to allow for cross site scripting of the plugin.
iStartSurf is an ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer (BHO) and Firefox/Chrome (plugin) and distributed through various monetization platforms during installation. The browser extension includes various features that will modify the default or custom settings of the browser including the home page, search settings and in some cases will modify Internet Explorer’s load time threshold, place a lock file within Firefox to prevent competing software from changing its settings as well as disable the browser’s Content Security Policy in order to allow for cross site scripting of the plugin.
iStartSurf homepage got on your computer after you have installed a freeware software (video recording/streaming, download-managers or PDF creators) that had bundled into their installation this browser hijacker.
For example, when you install VPlay, you will also agree to change your browser homepage toiStartSurf.com and default search engine to search.yahoo.com
However when you uninstall VPlay from your computer, your web browser’s default settings will not be restored. This means that you’ll have to remove iStartSurf.com homepage from your favorite web browser manually.
For example, when you install VPlay, you will also agree to change your browser homepage toiStartSurf.com and default search engine to search.yahoo.com
However when you uninstall VPlay from your computer, your web browser’s default settings will not be restored. This means that you’ll have to remove iStartSurf.com homepage from your favorite web browser manually.
You should always pay attention when installing software because often, a software installer includes optional installs, such as this iStartSurf.com browser hijacker. Be very careful what you agree to install.
Always opt for the custom installation and deselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place. It goes without saying that you should not install software that you don’t trust.
Always opt for the custom installation and deselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place. It goes without saying that you should not install software that you don’t trust.
How to remove iStartSurf.com (Virus Removal Guide)
This page is a comprehensive guide, which will remove iStartSurf.com from your Internet Explorer, Firefox and Google Chrome.
Please perform all the steps in the correct order. If you have any questions or doubt at any point,STOP and ask for our assistance.
STEP 1: Uninstall iStartSurf malicious programs from your computer
STEP 2: Remove iStartSurf.com virus from Internet Explorer, Firefox and Chrome
STEP 3:Clean up the various Windows shortcuts that have been hijacked by iStartSurf.com virus
STEP 4: Remove iStartSurf.com browser hijacker from your computer with AdwCleaner
STEP 5: Remove iStartSurf.com virus with Malwarebytes Anti-Malware Free
STEP 6: Double-check for the iStartSurf.com infection with HitmanPro
Please perform all the steps in the correct order. If you have any questions or doubt at any point,STOP and ask for our assistance.
STEP 1: Uninstall iStartSurf malicious programs from your computer
STEP 2: Remove iStartSurf.com virus from Internet Explorer, Firefox and Chrome
STEP 3:Clean up the various Windows shortcuts that have been hijacked by iStartSurf.com virus
STEP 4: Remove iStartSurf.com browser hijacker from your computer with AdwCleaner
STEP 5: Remove iStartSurf.com virus with Malwarebytes Anti-Malware Free
STEP 6: Double-check for the iStartSurf.com infection with HitmanPro
STEP 1 : Uninstall iStartSurf malicious programs from your computer
In this first step, we will try to identify and remove any malicious program that might be installed on your computer.
- To uninstall a program from Windows XP, Windows Vista or Windows 7, click the “Start” button, then click on the “Control Panel” menu option.
![Control Panel in Windows Start Menu [Image: Control Panel in Windows Start Menu]](http://malwaretips.com/blogs/wp-content/uploads/2014/01/windows-start-menu-control-panel.jpg)
If you are using Windows 8, simply drag your mouse pointer to the right edge of the screen, select Search from the list and search for “control panel” .Or you can right-click on a bottom left hot corner (formerly known as the Start button) and select Control Panel from there.![Type Control Panel in Windows 8 search box [Image: Type Control Panel in Windows 8 search box]](http://malwaretips.com/blogs/wp-content/uploads/2014/06/windows-8-uninstall.jpg)
- When the “Control Panel” window opens click on the “Uninstall a program” option under “Programs” category. This option is shown by the arrow in the image below. If you are using the “Classic View” of the Control Panel, then you would double-click on the “Programs and Features” icon instead.
![Click on Uninstall a program [Image: Uninstall a program]](http://malwaretips.com/blogs/wp-content/uploads/2013/03/uninstall-a-program-windows.jpg)
- When the “Programs and Features” or the “Uninstall a Program” screen is displayed, scroll through the list of currently installed programs and uninstall iStartSurf uninstaller,iStartSurf NewTab, Wsys Control WPM17.8.0.3159, Extended Protection, IePluginService,SupTab and any other recently installed unknown program from your computer.
To view the most recently installed programs, you can click on the “Installed On” column to sort your program by the installation date. Scroll though the list, and uninstall any unwanted or unknown programs.![Uninstall iStartSurf from Windows [Image: Uninstall iStartSurf program from Windows]](http://malwaretips.com/blogs/wp-content/uploads/2014/07/istartsurf-uninstall.jpg)
Depending on what program has installed the iStartSurf.com adware infection, the above program may have a different name or not be installed on your computer. If you cannot find any unwanted or unknown programs on your machine, then you can proceed with the next step.
If you are having issues while trying to uninstall the iStartSurf.com program, you can use Revo Uninstaller to completely remove this unwanted program from your machine.
STEP 2: Remove iStartSurf.com virus from Internet Explorer, Firefox and Google Chrome
Remove iStartSurf.com virus from Internet Explorer
You can reset Internet Explorer settings to return them to the state they were in when Internet Explorer was first installed on your PC.
- Open Internet Explorer, click on the “gear icon”
![[Image: icongear.jpg]](http://malwaretips.com/images/removalguide/icongear.jpg) in the upper right part of your browser, then click again on Internet Options.
in the upper right part of your browser, then click again on Internet Options.![Click on the Gear Icon then on Internet Options [Image: Internet Options in Internet Explorer]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/Internet-Options-Internet-Explorer.jpg)
- In the “Internet Options” dialog box, click on the “Advanced” tab, then click on the “Reset” button.
![In the Advanced tab click on the Reset button [Image: Reset Internet Explorer]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/Reset-Internet-Explorer.jpg)
- In the “Reset Internet Explorer settings” section, select the “Delete personal settings” check box, then click on “Reset” button.
![Click on the Reset button to revert IE to its default settings [Image: Reset Internet Explorer to its default settings]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/reset-button-Internet-Explorer.jpg)
- When Internet Explorer has completed its task, click on the “Close” button in the confirmation dialogue box. You will now need to close your browser, and then you can open Internet Explorer again.
![Click on the Close button [Image Reset Internet Explorer settings]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/Close-button-Reset.jpg)
Remove iStartSurf.com virus from Mozilla Firefox
If you’re having problems with Firefox, resetting it can help. The reset feature fixes many issues by restoring Firefox to its factory default state while saving your essential information like bookmarks, passwords, web form auto-fill information, browsing history and open tabs.
- In the upper-right corner of the Firefox window, click the Firefox menu button (
![Firefox Menu button [Image: Firefox Menu button]](http://malwaretips.com/blogs/wp-content/uploads/2014/04/Firefox-menu-button.png) ), then click on the “Help” (
), then click on the “Help” (![Firefox Help button [Image: Firefox Help button]](http://malwaretips.com/blogs/wp-content/uploads/2014/04/Firefox-Help.png) ) button.
) button.![Click on the Menu button then question mark button [Image: Click on the Menu button then Help]](http://malwaretips.com/blogs/wp-content/uploads/2014/04/Firefox-Help-button.jpg)
- From the Help menu, choose Troubleshooting Information.
If you’re unable to access the Help menu, type about:support in your address bar to bring up the Troubleshooting information page.![Troubleshooting Information in Firefox [Image: Troubleshooting Information in Firefox]](http://malwaretips.com/blogs/wp-content/uploads/2014/04/Firefox-Troubleshooting-Information.jpg)
- Click the “Reset Firefox” button in the upper-right corner of the “Troubleshooting Information” page.
![Reset Firefox to its default settings [Image: Reset Firefox to its default settings]](http://malwaretips.com/blogs/wp-content/uploads/2014/04/Reset-Firefox-button.jpg)
- To continue, click on the “Reset Firefox” button in the new confirmation window that opens.
![Click on the Reset Firefox button [Image: Click on the Reset Firefox button]](http://malwaretips.com/blogs/wp-content/uploads/2014/04/Reset-Firefox-to-default-settings.jpg)
- Firefox will close itself and will revert to its default settings. When it’s done, a window will list the information that was imported. Click on the “Finish“.
Note: Your old Firefox profile will be placed on your desktop in a folder named “Old Firefox Data“. If the reset didn’t fix your problem you can restore some of the information not saved by copying files to the new profile that was created. If you don’t need this folder any longer, you should delete it as it contains sensitive information.
Remove iStartSurf.com virus from Google Chrome
- Remove iStartSurf.com extensions from Google Chrome.
Click on the “Chrome menu button” ( ) on the browser toolbar, select “Tools“, and then click on “Extensions“.
) on the browser toolbar, select “Tools“, and then click on “Extensions“.![Extensions menu in Chrome [Image: Extensions menu in Chrome]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/Google-Chrome-extensions.jpg)
In the Extensions tab, remove iStartSurf NewTab, Extended Protection 1.9, Lightning Newtab and any other unknown extensions by clicking the trash can![Remove an extension from Chrome [Image: Remove an extension from Chrome]](http://malwaretips.com/blogs/wp-content/uploads/2013/07/Trash-Can-Chrome.png) icon.
icon.
Basically, if you have not installed a Chrome extension, you should remove it from your web browser.![iStartSurf Chrome extensions [Image: iStartSurf Chrome extensions]](http://malwaretips.com/blogs/wp-content/uploads/2014/05/malicious-extensions.jpg)
- Set Google Chrome default search engine from Yahoo Search to Google.
Click the Chrome menu button, then select Settings and click on Manage search engines in the Search section.
button, then select Settings and click on Manage search engines in the Search section.
In the Search Engines dialog that appears, select Google and click the Make Default button that appears in the row.![Yahoo Search in Google Chrome [Image: Yahoo Search in Google Chrome]](http://malwaretips.com/blogs/wp-content/uploads/2013/11/Yahoo-Search-Chrome.jpg)
Search for Yahoo Search in the Search Engines list, and click the X button that appears at the end of the row.![Yahoo Search Chrome removal [Image: Yahoo Search Chrome removal]](http://malwaretips.com/blogs/wp-content/uploads/2013/11/Yahoo-Search-Chrome-removal.jpg)
- Change Google Chrome homepage from iStartSurf.com to its default.
iStartSurf has modified your Google settings to open their webpage whenever you start your browser, so we will need to revert this change.
Click the Chrome menu button, then select Settings and click on One the New Tab page in the On Startup section.
button, then select Settings and click on One the New Tab page in the On Startup section.![Change Google Chrome homepage to its default [Image: Change Google Chrome homepage to its default]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Chrome-default-page.jpg)
STEP 3: Clean up the various Windows shortcuts that have been hijacked by iStartSurf.com virus
This infection has hijacked your browser shortcuts, so in this step we will need to manually clean them by removing the iStartSurf.com argument
- Search for your browser shortcut (Desktop, Taskbar or Start Menu Shortcut), then right click on it and select Properties.
![Desktop Shortcut properties [Image: Firefox Shortcut properties]](http://malwaretips.com/blogs/wp-content/uploads/2013/02/shortcut-properties.jpg)
To view the Properties menu for the browser shortcuts pinned to your Task Bar, right-click on the browser shortcut from the Taskbar, then right-click again on the browser icon as see in the below image. Alternatively, you can just Unpin the browser shortcut from your task bar, then you can add it back after you have removed the “iStartSurf.com” argument from the original browser shortcut.![Right click on browser icon from Taskbar and select Properties [Image: taskbar shortcut hijacker]](http://malwaretips.com/blogs/wp-content/uploads/2013/04/taskbar-shortcuts-hijack.jpg)
- In the Shortcut tab, in the Target field, remove the http://iStartSurf.com argument. Basically, there should be only the path to browser executable file. Nothing more.
These are the default shortcut path that should be in your Target box, if the iStartSurf.comargument is there, then you should remove it.If you are using this browser: In the Target field you should have: Internet Explorer “C:\Program Files\Internet Explorer\iexplore.exe” Chrome “C:\Program Files\Google\Chrome\Application\chrome.exe” for Windows 32 bit OR “C:\Program Files (x86)\Google\Chrome\Application\chrome.exe” for Windows 64-bit Firefox “C:\Program Files\Mozilla Firefox\firefox.exe” for Windows 32-bit OR “C:\Program Files (x86)\Mozilla Firefox\firefox.exe” for Windows 64-bit ![iStartSurf.com hijack [Image: iStartSurf.com hijack]](http://malwaretips.com/blogs/wp-content/uploads/2014/07/istartsurf-hijack.jpg)
STEP 4: Remove iStartSurf.com browser hijacker with AdwCleaner
The AdwCleaner utility will scan your computer and web browser for the “iStartSurf.com” malicious files, browser extensions and registry keys, that may have been installed on your computer without your knowledge.
- You can download AdwCleaner utility from the below link.
ADWCLEANER DOWNLOAD LINK (This link will open a new web page from where you can download AdwCleaner) - Before starting AdwCleaner, close all open programs and internet browsers, then double-click on the AdwCleaner icon.

If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run. - When the AdwCleaner program will open, click on the “Scan” button as shown below.

AdwCleaner will now start to search for the “iStartSurf.com” malicious files that may be installed on your computer. - To remove the “iStartSurf.com” malicious files that were detected in the previous step, please click on the “Clean” button.

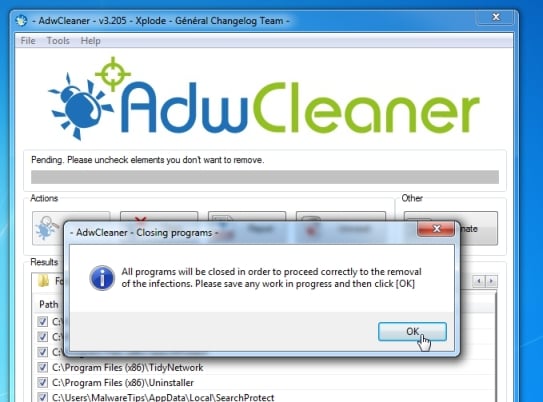
- AdwCleaner will now prompt you to save any open files or documents, as the program will need to reboot the computer. Please do so and then click on the OK button.
STEP 5: Remove iStartSurf.com virus with Malwarebytes Anti-Malware Free
Malwarebytes Anti-Malware Free uses industry-leading technology to detect and remove all traces of malware, including worms, Trojans, rootkits, rogues, dialers, spyware, and more.
It is important to note that Malwarebytes Anti-Malware works well and should run alongside antivirus software without conflicts.
It is important to note that Malwarebytes Anti-Malware works well and should run alongside antivirus software without conflicts.
- You can download download Malwarebytes Anti-Malware from the below link.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK (This link will open a new web page from where you can download Malwarebytes Anti-Malware Free) - Once downloaded, close all programs, then double-click on the icon on your desktop named “mbam-setup-consumer-2.00.xx” to start the installation of Malwarebytes Anti-Malware.
![Malwarebytes Anti-Malware setup program [Image: Malwarebytes Anti-Malware setup program]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/Malwarebytes-Anti-Malware-Setup.jpg)
 You may be presented with a User Account Control dialog asking you if you want to run this file. If this happens, you should click “Yes” to continue with the installation.
You may be presented with a User Account Control dialog asking you if you want to run this file. If this happens, you should click “Yes” to continue with the installation. - When the installation begins, you will see the Malwarebytes Anti-Malware Setup Wizardwhich will guide you through the installation process.
![Malwarebytes Anti-Malware Setup Wizard [Image: Malwarebytes Anti-Malware Setup Wizard]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-2-0-installation.jpg)
To install Malwarebytes Anti-Malware on your machine, keep following the prompts by clicking the “Next” button.![Malwarebytes Anti-Malware Final Setup Screen [Image: Malwarebytes Anti-Malware Final Setup Screen]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-2-0-final-screen.jpg)
- Once installed, Malwarebytes Anti-Malware will automatically start and you will see a message stating that you should update the program, and that a scan has never been run on your system. To start a system scan you can click on the “Fix Now” button.
![[Image: Click on the Fix Now button to start a scan]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-fix-now.jpg)
Alternatively, you can click on the “Scan” tab and select “Threat Scan“, then click on the“Scan Now” button.![Malwarebytes Anti-Malware Threat Scan [Image: Malwarebytes Anti-Malware Threat Scan]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-threat-scan-option.jpg)
- Malwarebytes Anti-Malware will now check for updates, and if there are any, you will need to click on the “Update Now” button.
![Click on Update Now to update Malwarebytes Anti-Malware [Image: Click on Update Now to update Malwarebytes Anti-Malware]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-2-0-update-now.jpg)
- Malwarebytes Anti-Malware will now start scanning your computer for the iStartSurf.com virus. When Malwarebytes Anti-Malware is scanning it will look like the image below.
![Malwarebytes Anti-Malware while performing a scan [Image: Malwarebytes Anti-Malware while performing a scan]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-scan.jpg)
- When the scan has completed, you will now be presented with a screen showing you the malware infections that Malwarebytes’ Anti-Malware has detected. To remove the malicious programs that Malwarebytes Anti-malware has found, click on the “Quarantine All” button, and then click on the “Apply Now” button.
![Remove the malware that Malwarebytes Anti-Malware has detected [Image: Remove the malware that Malwarebytes Anti-Malware has found]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-potential-threat-detected.jpg)
Please note that the infections found may be different than what is shown in the image. - Malwarebytes Anti-Malware will now quarantine all the malicious files and registry keys that it has found. When removing the files, Malwarebytes Anti-Malware may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot your computer, please allow it to do so.
![Malwarebytes Anti-Malware asking to reboot your computer [Image: Malwarebytes Anti-Malware while removing viruses]](http://malwaretips.com/blogs/wp-content/uploads/2014/02/malwarebytes-anti-malware-remove-virus.jpg)
After your computer will restart, you should open Malwarebytes Anti-Malware and perform another “Threat Scan” scan to verify that there are no remaining threats
STEP 6: Double check for the iStartSurf.com infection with HitmanPro
HitmanPro is a second opinion scanner, designed to rescue your computer from malware (viruses, trojans, rootkits, etc.) that have infected your computer despite all the security measures you have taken (such as anti virus software, firewalls, etc.). HitmanPro is designed to work alongside existing security programs without any conflicts. It scans the computer quickly (less than 5 minutes) and does not slow down the computer.
- You can download HitmanPro from the below link:
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download HitmanPro) - Double-click on the file named “HitmanPro.exe” (for 32-bit versions of Windows) or “HitmanPro_x64.exe” (for 64-bit versions of Windows). When the program starts you will be presented with the start screen as shown below.
![HitmanPro startup screen (Click Next) [Image: HitmanPro start-up screen]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-install.jpg)
Click on the “Next” button, to install HitmanPro on your computer.![HitmanPro installation options (Click Next) [Image: HitmanPro setup options]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmapro-start-scan.jpg)
- HitmanPro will now begin to scan your computer for iStartSurf.com malicious files.
![HitmanPro scanning for iStartSurf.com virus [Image: HitmanPro scanning for malware]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-scanning.jpg)
- When it has finished it will display a list of all the malware that the program found as shown in the image below. Click on the “Next” button, to remove iStartSurf.com malware.
![HitmanPro scan results (Click Next) [Image: HitmanPro scan results]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-scan-results.jpg)
- Click on the “Activate free license” button to begin the free 30 days trial, and remove all the malicious files from your computer.
![Click on the Activate free license button [Image: HitmanPro Activate Free License]](http://malwaretips.com/blogs/wp-content/uploads/2014/03/hitmanpro-activation.jpg)
Your computer should now be free of the iStartSurf.com infection. If your current anti-virus solution let this infection through, you may want to consider purchasing the Premium version of Malwarebytes Anti-Malware to protect against these types of threats in the future, and perform regular computer scans with HitmanPro.
If you are still experiencing problems while trying to remove iStartSurf.com hijacker from your machine, please start a new thread in our Malware Removal Assistance forum.
If you are still experiencing problems while trying to remove iStartSurf.com hijacker from your machine, please start a new thread in our Malware Removal Assistance forum.
IT’S YOUR TURN TO HELP!
If we have managed to help you with your computer issues, then it's your duty to let other people know that this article will help them!
You can share this article on Facebook,Twitter or Google Plus by using the below buttons.
You can share this article on Facebook,Twitter or Google Plus by using the below buttons.
Monday, October 6, 2014
A complete guide to Wake On LAN for ConfigMgr 2007 and ConfigMgr 2012
Wake on LAN and so that there isn’t a need a rely on multiple resources when trying to implement this in your environment.
What’s covered
1. What Wake on LAN is and how it works
2. The requirements for Wake on LAN
3. Wake On LAN in a multiple site hierarchy
4. General configuration
5. Activating Wake on LAN
6. Monitoring
7. Troubleshooting
8. Limitations
What Wake on LAN is and how it works
So what is Wake on LAN? Wake on LAN is essentially a network request or a network message to turn on a computer when it is in hibernate, sleep mode or turned off.
ConfigMgr supports the sleep states documented in the TechNet article here:
Sleep States for Wake On LAN (http://technet.microsoft.com/en-us/library/bb693821.aspx)
However, it also depends upon the architecture of the computer. It is a technology developed by Intel and IBM and is integrated into Microsoft Configuration Manager.
Wake on LAN is implemented in an environment using a special data packet known as Magic Packet. A Magic Packet consists of 6 bytes of all 255 (FF FF FF FF FF FF), followed by sixteen repetitions of the target computer's MAC address. Below is an example of how a magic packet frame looks like captured using a third party network sniffer tool:
For a machine to wake up, it can be in a shutdown, sleep or any other supported state, but it must also be connected to power source. The Magic packet is sent to the computer where the network card then signals the motherboard and the power supply to turn on the machine, similar to turning it on using a power button.
The requirements for Wake on LAN
The requirements can be divided into four categories and we’ll discuss each of them in brief:
1. Requirements for the ConfigMgr server
2. Requirements for the network
3. Requirements for the client
4. Hardware Inventory
The requirements for the ConfigMgr server are that the server must be up and running, the Management Point needs to be working properly, Wake on LAN must be enabled and the port being used must not be blocked on the firewall.
The requirements for the network are that switches and routers must be configured to allow the broadcast network packets if the chosen method is a subnet directed broadcast, and they should be allowed to forward the UDP packets if the chosen method is Unicast. Apart from that, the port being used must be opened on the router and the switch.
The requirements for the client are that the communication between the client and the management point should be healthy (e.g. the client should be able to download the policy from the Management point, etc.), Wake on LAN must be enabled in the BIOS and the network card must support Wake on LAN and have the feature enabled.
Apart these three requirements there is another very important dependency and that is Hardware Inventory. The Hardware Inventory information sent by the client includes the IP address, MAC address and subnet address. The Hardware Inventory information sent by the client (consisting of the MAC address and the subnet address in case of subnet directed broadcast, and the IP address and MAC address in the case of unicast) must be the actual MAC address and IP or subnet address on the client.
Wake On LAN in a multiple site hierarchy
If you wish to implement Wake On LAN in a multiple site hierarchy then you must be aware of following three considerations:
1. Wake-up packet transmissions are sent only from primary site servers. You cannot configure secondary site servers or other computers acting as proxies to send wake-up packets.
2. If you are enabling Wake On LAN on a child site, deployments and advertisements that are inherited from a parent site will include the Enable Wake On LAN configuration.
3. If the child site is not enabled for Wake On LAN, client computers in that site will not be sent wake-up packets.
General Configuration
Server configuration
Now that we’ve covered some of the basics, let’s go through a simple step-by-step configuration of Wake on LAN.
To enable Wake on LAN in ConfigMgr 2007 or ConfigMgr 2012, go to the site properties –> Wake On LAN and put a check mark next to “Enable Wake on LAN for this site” as shown in the screenshot below.
Choose the first or second option if you want to wake machines using AMT. Choose the first or the third option if you want to wake up the machine using Wake on LAN.
There are two transmission methods for WOL magic packets:
Subnet Directed Broadcast: In this method of transmission, the subnet address and the MAC address is retrieved from Hardware Inventory and wake-up packets are targeted to the subnet where they are broadcast to all the machines within that subnet. This method will fail if the machine changed its subnet and the ConfigMgr server has not yet received the updated Hardware Inventory with the information of its latest subnet. However, it should not fail if the machine has changed its IP address because the wake-up packets hit the subnet address rather than the IP address and should still reach the client. By default, subnet broadcasting is disabled on routers and switches, therefore it is important to ensure that is enabled if this is the method you choose. Also keep in mind that subnet-directed broadcasts are not supported with IPv6 addresses. For security reasons and to prevent smurf attacks, Microsoft highly recommends that you use a non-default port with this method of transmission.
Unicast: With this method of transmission, the IP address and the MAC address is retrieved from Hardware Inventory and wake-up packets are targeted directly to the IP address on the subnet. If the target machine has changed its IP address and Hardware Inventory has yet to update, the wake-up packet will reach the destination IP but will fail because the MAC address is different. Be sure to configure switches to forward UDP packets, and verify with your hardware vendor that older network cards support this method of transmission. In order for this method to be successful, entries for the client machines should be in the ARP cache of the router or the site server. More details on this are mentioned in the last section covering troubleshooting.
Which method should I use?
Both transmission methods have their pros and cons and it depends on your environment as to which method you should opt to use.
The advantage of subnet broadcasting is that the success rate is very high if the target machines frequently change their IP addresses. For this reason it is preferred. This is the original method of sending wake-up packets so it works with almost all sleep states. The disadvantage is that it is less secure, it consumes more network bandwidth, it requires reconfiguration of routers and it does not supports IPv6 addresses.
The advantage of unicast is that it’s more secure, it consumes less bandwidth, it supports both IPv4 and IPv6 addresses and requires no reconfiguration on the routers. The disadvantages of unicast are that it can be less successful, switches must be configured to forward UDP packets, and it may not wake-up machines from all sleep states.
After reading the advantages and disadvantages, if you have decided to use the Unicast method but the clients in your environment frequently change their IP addresses, it is recommended that you increase the DHCP lease time and shorten the Hardware Inventory schedule, however doing so can impact traffic on your network.
After enabling WOL and choosing the transmission method, Please choose the port number as shown in the screen shot below. By default, ConfigMgr uses UDP port 9, however you can use a custom UDP port of your choice. Whichever port you choose, please ensure that it’s not blocked on any firewall or intervening routers.
Client Configuration
After enabling and configuring Wake on LAN on server side, let’s proceed with configuring it on the client side.
On the ConfigMgr clients, ensure that Wake on LAN is enabled in the system BIOS. You may see different terminologies for WOL depending on the manufacturer (e.g. Remote Wake-up, Wake on LAN, Wake on PCI card etc.).
In addition to the BIOS, the network card must be configured to support Magic or wake-up packets. To do this, go to Start –> Run –> devmgmt.msc –> Device Manager –> Network Adapters, then right-click the network card and go to Properties. If your card has an advanced tab, ensure that WOL is enabled as per the screenshot below.
On the Power Management tab of the Network Card, please ensure that all three options shown below are checked to allow the NIC to wake the machine.
I can’t really tell you if there is a way in which you can enable Wake on LAN in the BIOS on multiple machines in your environment, however you can use Fix it tool 55017 from http://support.microsoft.com/kb/2740020 to enable power management on all of the machines in your environment. This Fix it tool can be deployed using a Group Policy, ConfigMgr, etc.
Network Configuration
As mentioned earlier, routers and switches must allow the port configured for Wake on LAN. In addition, intervening routers must allow the broadcast of wake-up packets if the chosen transmission method is subnet directed broadcast. Switches must be configured to forward UDP packets if the chosen transmission method is Unicast.
Hardware Inventory
After configuring the above settings, verify that the machine being tested has successfully reported its inventory. You can do this by right-clicking the machine in the console –> Start –> Resource Explorer –> Hardware –> Network Adapter configuration. In the screenshot below you can see that the client is sending its IP address, subnet address and MAC address. The Hardware Inventory information sent by the client consists of the MAC address and the subnet address in the case of subnet directed broadcast, and the IP address and MAC address in the case of unicast. These must be the same as the actual MAC address and IP or subnet address of the client. If there is mismatch between the inventory information and the details on the client, Wake on LAN will fail because the Magic Packet will fail to locate the machine. In such a case you may have to initiate the hardware inventory cycle on the client so that it sends fresh inventory information.
Activating Wake on LAN
After meeting the above requirements, your client should probably be capable of using WOL, however you must still activate Wake on LAN so your clients can turn on when they receive a Software Update, Package or Task Sequence.
Please note that in ConfigMgr 2007, Advertisements/Deployments should be configured as Mandatory and in ConfigMgr 2012, Deployments must be configured as “Required” for Wake on LAN to work.
Configuring Wake on LAN in ConfigMgr 2007
To configure a Software Update for Wake on LAN:
1. In the Configuration Manager console, navigate to System Center Configuration Manager / Site Database / Computer Management / Software Updates / Deployments.
2. Right-click the deployment you want to configure for Wake on LAN and then click Properties.
3. On the Schedule tab, select the option Enable Wake on LAN.
4. Click OK.
To configure a Software Distribution mandatory advertisement for Wake on LAN:
1. In the Configuration Manager console, navigate to System Center Configuration Manager / Site Database / Computer Management / Software Distribution / Advertisements.
2. Right-click the advertisement that supports the Software Distribution you want to enable for Wake on LAN and then click Properties.
3. On the Schedule tab, select the option Enable Wake on LAN.
To configure a Task Sequence mandatory advertisement for Wake on LAN:
1. In the Configuration Manager console, navigate to System Center Configuration Manager / Site Database / Computer Management / Software Distribution / Advertisements.
2. Right-click the advertisement that supports the operating system deployment that you want to enable for Wake on LAN and then click Properties.
3. On the Schedule tab, select the option Enable Wake on LAN.
Configuring Wake on LAN in ConfigMgr 2012
To configure a software update for Wake on LAN:
1. In the Configuration Manager console, navigate to Software Library/ Software Updates/ Software Update Groups
2. Right-click on the Software Update Group and click on deploy
3. On the Deployment Settings- Type of Deployment Settings must be configured to “Required” and “Use Wake on-LAN to wake up clients for required deployments” should be checked.
Configuring an Application or a Package for Wake on LAN:
1. In the Configuration Manager console, navigate to Software Library/ Application Management/ Applications or Packages
2. Right-click on the Application or the Package and click on deploy
3. On the Deployment Settings- Purpose must be configured to “Required” and “Send Wake-up Packets” should be checked.
Configuring a Task Sequence for Wake on LAN:
1. In the Configuration Manager console, navigate to Software Library/ Operating Systems/ Task Sequences
2. Right-click on the Task Sequence and click on deploy
3. On the Deployment Settings- Purpose must be configured to “Required” and “Send Wake-up Packets” should be checked.
Monitoring
In ConfigMgr we have two logs on the site server to monitor Wake on LAN activity: Wolmgr.log and Wolcmgr.log. Wolmgr.log basically shows us the status of the Wake on LAN manager component but it’s the Wolcmgr.log which shows us the status of the Wake on LAN packets.
If the wake-up packets are being sent out, we get STATMSG=6504 in wolcmgr.log as per the screenshot below.
Once the sending of the packets is completed we receive STATMSG=6505 in wolcmgr.log.
Below is a table of Message ID’s with the description you will find in Wolcmgr.log. These ID’s will assist you in understanding the status of wake-up packets in the event of a success or a failure.
In addition to the above logs, you can also use a Network Monitor trace or any third party WOL sniffer tool (e.g. http://profshutdown.com/download.aspx) to verify if packets are being sent out.
Troubleshooting
Below are some tips for you that I have learned from my experience with WOL. However, before we begin to troubleshoot Wake on LAN issues, we should always narrow down where exactly the problem is. We need to determine if the problem is at the ConfigMgr server, on the Network or at the client end.
First of all, be sure that you read through each section above to make sure you have the basics covered. And when testing, always have at least two or more machines to test with instead of just one.
For specific troubleshooting I’ll take a shortcut here to save some time.
- If you are unable to wake a machine using ConfigMgr WOL, however your are able to wake it using a 3rd party Wake On LAN utility, most likely the machine is capable of WOL and the issue lies either in the Hardware Inventory, on the server side or in the network.
- If you are able to wake a machine on the same subnet as the Site server, however it’s not waking on a different subnet then most likely the issue is with the switch or the router.
- Verify that problematic machines are communicating with the Management point and are able to download policies. (e.g. check Ccmexec.log, ClientIDManagerstartup.log, PolicyAgent.log etc.).
- Ensure that the port you specified for Wake on LAN is not blocked at the firewall or on any intervening device on the network. You might also try an alternate port for testing purposes.
- Check the binding order of the network cards if there are more than one on the ConfigMgr server or client. Also ensure that all network cards (or at least the one in use) are configured to forward and receive Wake-up Packets.
- If you are using the subnet directed broadcast transmission method, ensure that Broadcast is enabled on intervening routers and switches.
- If you are using Unicast, ensure that switches and routers are configured to forward UDP packets.
- I have come across a specific scenario several times where machines do not wake-up when using Unicast because routers are unable to resolve the IP address to MAC address since the entry of the machine does not exist in the ARP Table on the router. ARP is a mapping of MAC and IP addresses, and by running the command Arp –a on the Router/Site server we can verify if the entry of the machine exists in the ARP cache of the Router/Site Server. To verify is the issue is with ARP cache you can manually add the entry of a machine to the ARP cache of the ConfigMgr site server by running the command arp –s <ip_address> <mac_address> (e.g. arp -s 192.168.x.xxx 00-2x-5x-C1-xx-xx) on the ConfigMgr site server. This will override the ARP cache of the router. To fix this issue for several machines you might have to increase the ARP Cache Stale Timeout period and ARP Cache Update Timeout period. The default time out period for most Routers and Switches is 240 seconds.
- If you have enabled the Time Zone Hardware Inventory class you may come across an issue where a machine wakes-up in a different time zone. In such a case please ensure that the time zone in the Hardware Inventory and the actual time zone of the machine is the same.
Limitations
- Using ConfigMgr Wake On LAN, you will not be able to wake-up machines which are on the Internet.
- You will not be able to wake-up Bare Metal machines.
- Wake On LAN transmissions are always sent at the scheduled time, ignoring any maintenance windows that might be in effect on a client computer.
That’s it for Wake on LAN. Thanks for going through this article and kindly drop me a comment if I forgot to add something.












