Thursday, September 25, 2014
Wednesday, September 24, 2014
Tuesday, September 23, 2014
How to Reset Outlook 2007 to Its Default
If you use Outlook 2007 to handle emails in your business, you can change its settings, views, tool bars and even menus. This enables you to personalize Outlook and helps you save valuable time when searching for certain items or performing various actions. If you want to restore the original settings, views, menus and tool bars, you need to reset Microsoft Office Outlook 2007. The software stores its settings in a configuration file on your hard disk and is able to rebuild this file if it can't find it. The new configuration file contains only default settings.
Step 1Close Microsoft Outlook 2007.
Step 2Click the Start button and select "Computer" from the menu to open the native file manager. Step 3Select the system drive -- usually "C:" -- from the left pane.
Step 4Open the "Users\UserName\AppData\Roaming\Microsoft\Outlook" folder, where "UserName" is the name of your user account.
Step 5Right-click the "outcmd.dat" file and select "Rename" from the context menu.
Step 6Type "outcmd.old" as the new name and press "Enter" to rename the file.
Step 7Launch Microsoft Outlook 2007, a new outcmd.dat file is automatically created, and all settings are reset to their default values.
Tip
- You can use any other name when you rename the "outcmd.dat" file.
Warning
- You will lose all your custom settings when you reset the software.
Thursday, September 18, 2014
SOLUTION: Recover/import Windows Live Mail Contacts to new computer
So today I was tasked with recovering a client’s contacts stored in a Windows Live Mail edb database for the first time. At first, it seemed like a daunting task–primarily because I could not get a (previously) popular solution involving the now-deprecated EseDbViewer to work. That’s because, as I later discovered, the process must be performed on the original PC in order for it to work; if you try it using the recovered files on another machine, it simply fails.
Fortunately, as is usually the case, there is another way around this problem, and it’s actually quite easy. The goal is to get the contacts from the edb into a readable .csv (Comma Separated Values) file for import into Windows Live Mail. And a company known as Nirsoft (who makes a number of helpful tools, often of forensic nature) has a program that works perfectly.
It’s called LiveContactsView, and it’s designed for viewing Windows Live Messenger contacts. However, Windows Live Mail uses the same format for storing its contacts, so it works here, too.
Here’s the full process:
- Download LiveContactsView.
- Recover the original Windows Live Mail contacts database files from the failed PC/original drive:
- They’re located in %LOCALAPPDATA%\Microsoft\Windows Live Contacts\{GUID}\DBStore, where %LOCALAPPDATA% is an environment variable equivalent to \Users\{USERNAME}\AppData\Local\ on the drive, and {GUID} is a random string assigned to the original user’s profile.
- Using LiveContactsView, open the contacts.edb file from the DBStore folder.
- Select all fields within the list view.
- Export the items to a .csv file.
- Import the .csv file into the mail client of your choice.
SOLUTION: “This is Microsoft Support” telephone scam – Computer ransom lockout
A trend of the past couple of years has been for scammers to contact computer owners directly via telephone in the United States in an effort to convince them that there is a problem with their PC and they’ll need to pay to have it fixed. In general, these people cannot fix anything, and instead they merely charge exorbitant fees for absolutely nothing. In other words, they scam you.
The call generally goes something like this:
In this case, it’s mere guesswork, and it’s not even correct most of the time. The Event Log is supposed to log warnings and errors, and even on the healthiest of PCs there are plenty of Error Events that can be safely ignored, as they often don’t amount to anything. The important thing to remember is to never trust someone who calls you about a problem with your PC, and never, EVER let them connect remotely to your PC.
If you do make the mistake of letting them connect, but then you happen to get cold feet and refuse to pay the $180+ they request via credit card, the next thing that happens isn’t pretty. This scammer proceeded to actually follow through on his promise of the PC “not working” if they don’t agree to have him fix it, and so in a few quick steps, behind the user’s back, he enacted what is known as SysKey encryption on the SAM registry hive.
SysKey encryption is a little-known feature of Windows which allows administrators to lock out access to the Security Accounts Manager (SAM) registry hive so that login specifics cannot be stolen and the PC cannot be accessed without knowing the proper credentials. The problem is, unlike other scams, there is no way around the problem; you can’t simply remove the password, as the actual SAM hive has been encrypted entirely by the process. If your Windows installation has had SysKey activated, you’ll see the following message:
 The ONLY solution is to find a clean copy of the registry hives from before this occurred. This scammer knew this, however, and as such, he took an extra step to block any repair or recovery attempts: he deleted all System Restore points on the machine, which normally house backup copies of the registry hives.
The ONLY solution is to find a clean copy of the registry hives from before this occurred. This scammer knew this, however, and as such, he took an extra step to block any repair or recovery attempts: he deleted all System Restore points on the machine, which normally house backup copies of the registry hives.
Unfortunately for him, I’m a much better technician. When the customer suspected foul play and decided to call me instead of proceeding, I immediately instructed them to power off the PC. Here’s how I fixed the problem without having to reinstall Windows.
FIRST, ensure you don’t have any Restore Points to work with:
In the case of my customer, it worked, and they were back in Windows, just like it never happened. Nice try, scammer. You’ll have to try harder to beat me though.
The call generally goes something like this:
- A foreigner with a thick Indian accent identifies himself as a member of Microsoft Support or similar.
- He informs you that you have a number of critical problems with your PC and that you will need to have it fixed.
- To convince you, he offers to connect remotely and pulls up your Event Log (eventvwr.msc). He then filters for Warnings, Errors, and Critical events and uses that as evidence that your PC will soon fail to work correctly if you do not pay him to correct it.
In this case, it’s mere guesswork, and it’s not even correct most of the time. The Event Log is supposed to log warnings and errors, and even on the healthiest of PCs there are plenty of Error Events that can be safely ignored, as they often don’t amount to anything. The important thing to remember is to never trust someone who calls you about a problem with your PC, and never, EVER let them connect remotely to your PC.
If you do make the mistake of letting them connect, but then you happen to get cold feet and refuse to pay the $180+ they request via credit card, the next thing that happens isn’t pretty. This scammer proceeded to actually follow through on his promise of the PC “not working” if they don’t agree to have him fix it, and so in a few quick steps, behind the user’s back, he enacted what is known as SysKey encryption on the SAM registry hive.
SysKey encryption is a little-known feature of Windows which allows administrators to lock out access to the Security Accounts Manager (SAM) registry hive so that login specifics cannot be stolen and the PC cannot be accessed without knowing the proper credentials. The problem is, unlike other scams, there is no way around the problem; you can’t simply remove the password, as the actual SAM hive has been encrypted entirely by the process. If your Windows installation has had SysKey activated, you’ll see the following message:
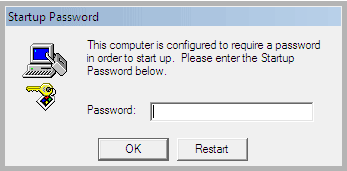
Startup PasswordThe window which appears looks like this:
This computer is configured to require a password in order to start up. Please enter the Startup Password below.

Unfortunately for him, I’m a much better technician. When the customer suspected foul play and decided to call me instead of proceeding, I immediately instructed them to power off the PC. Here’s how I fixed the problem without having to reinstall Windows.
FIRST, ensure you don’t have any Restore Points to work with:
- Check to ensure that the folder %SYSTEMROOT%\system32\config\RegBack exists. If so, continue. If not, stop and immediately contact a technician.
- Reboot the PC and repeatedly press F8 to reach the Advanced Startup Options menu.
- Choose Repair your Computer from the menu.
- Cancel the automatic repair attempt and instead instruct the system to perform a System Restore to a date prior to the incident occurring.
- POWER OFF your PC immediately.
- Boot to external media of some sort (NOT your Windows installation) and navigate to the %SYSTEMROOT%\system32\config folder.
- Backup the registry hives in this folder to a temporary location. The files are:
- SOFTWARE
- SYSTEM
- SAM
- SECURITY
- DEFAULT
- Navigate to %SYSTEMROOT%\system32\config\RegBack as mentioned earlier.
- Copy all registry hives from this folder (the same files as listed above) into the %SYSTEMROOT%\system32\config folder.
- Reboot the PC.
In the case of my customer, it worked, and they were back in Windows, just like it never happened. Nice try, scammer. You’ll have to try harder to beat me though.
Wednesday, September 17, 2014
Solution: Outlook Error: “Outlook Data File Could Not Be Accessed”
This is a pretty annoying little problem that I’ve seen at least a couple of times over the past several months.
It occurs when you attempt to sync within Outlook, normally following a data transfer or other procedure that involves bringing an existing .PST file into play without jumping through the hoops of importing the data into a new .PST shell.
The solution is actually easy, though it’s not necessarily easy to discover. All you have to do to solve the problem is select the folder to deliver mail to (Inbox) for each email account. Under the Account Settings dialog box within Outlook, there is a Change Folder button near the bottom. This is where the setting is changed.
But what if you can’t even open Outlook? You can still access the mail settings without running the program. The easiest way to do this is to click Start > Start Search > type mail and then open the Mail shortcut that appears under the Control Panel heading in the search results. This opens the standard Outlook mail dialog box as if you were running Outlook.
It occurs when you attempt to sync within Outlook, normally following a data transfer or other procedure that involves bringing an existing .PST file into play without jumping through the hoops of importing the data into a new .PST shell.
The solution is actually easy, though it’s not necessarily easy to discover. All you have to do to solve the problem is select the folder to deliver mail to (Inbox) for each email account. Under the Account Settings dialog box within Outlook, there is a Change Folder button near the bottom. This is where the setting is changed.
But what if you can’t even open Outlook? You can still access the mail settings without running the program. The easiest way to do this is to click Start > Start Search > type mail and then open the Mail shortcut that appears under the Control Panel heading in the search results. This opens the standard Outlook mail dialog box as if you were running Outlook.


